Lei Fengwang press: August 16, China's quantum satellite "Mozi" successfully launched, is also the world's first quantum scientific experimental satellite, so that quantum communications once again receive much attention. The essence of quantum communication to ensure information security is to distribute random keys. Only the sending and receiving parties can see, and any eavesdropping behavior will be discovered. But precisely because of this, this single function realization method has also been questioned with certain limitations—a large-scale quantum communication network is not feasible. What is the most important aspect of quantum communication? Is it safety or stability?
This article was written by two authors of Quantum Communication, authors of the Iron Stream, to refute the above-mentioned questioned views (the text is attached hereafter). Both sides have different opinions. The purpose of this article is not to be issued by Lei Fengwang (search for "Lei Feng Net" public number). However, it hopes to bring readers to think about quantum communication itself while bringing professional analysis.

The term “eavesdropping†often used in communication security is used vividly and accurately. The so-called burglary must be taken or not observed. Eavesdropping on communication lines, eavesdroppers generally have a stronger ability to receive, but we must also pay attention to eavesdroppers to know where the line. The eavesdropper's ability to keep both parties in communication while he is not being discovered is certainly of obvious benefit, but it is not that he cannot destroy communications. It can be said that eavesdropping is much more difficult than destruction, and anyone who has the ability to eavesdrop must have the ability to destroy.
In order to cope with the damage, the current network is more and more route, one path is broken and there is another path, one node is broken, and the rest of the network can not fail. At the same time, because the damage can be discovered, there is the opportunity to remediate it in time, and the loss can be considered as controllable. In terms of XX units, an optical fiber breaks and the business in one area will certainly stall many transactions, but it's okay to tell the customer that the money will not be lost; but if the eavesdropping really happened, the password was cracked, then this No one can guarantee that the loss will depend on the accounts involved, but also on the timely detection of eavesdropping .
Cryptologists use various methods to ensure that passwords cannot be cracked, and that they are relatively single-minded about the use of quantum communications. However, the viewpoint that "the primary purpose of communication is stability" proposed by Mr. Cao Zhengjun is not a cryptographer's style at all. Speaking from the author of a password application department, they described their role in the communication system as "First, guarantee that it is unreasonable, and then let it pass conditionally." As Mr. Cao said that "information security is not necessary for the vast majority of communications," I am very sorry that the author and he are not talking about the same topic, and there is no cryptographer.
As mentioned earlier, some aspects of the use of aspects, the following talk about quantum key distribution .
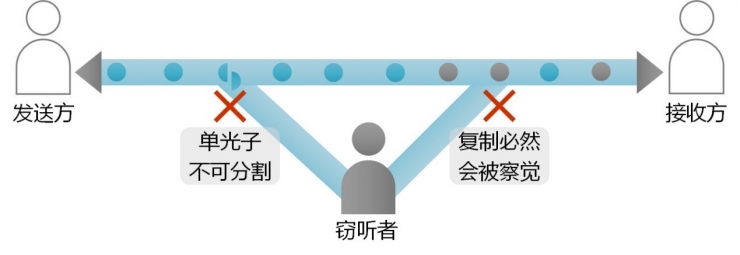
Typical schemes for quantum key distribution include single-photon state modulation-demodulation-key agreement several processes.
The so-called single-photon state modulation encodes "0" and "1" to some state of the photon;
Demodulation reads "0" and "1" by demodulating the optical path and the single photon detector;
Key agreement is to remove the unmatched examples of demodulation. According to the error rate, we can estimate the maximum probability that these photons are acquired by a third party and then use mathematical means to remove the risk.
In fact, this process has no signal security, because the signal loss ratio is currently over 90%. As for the negotiation process, I feel that it is more accurate to reject information than to abandon the signal.
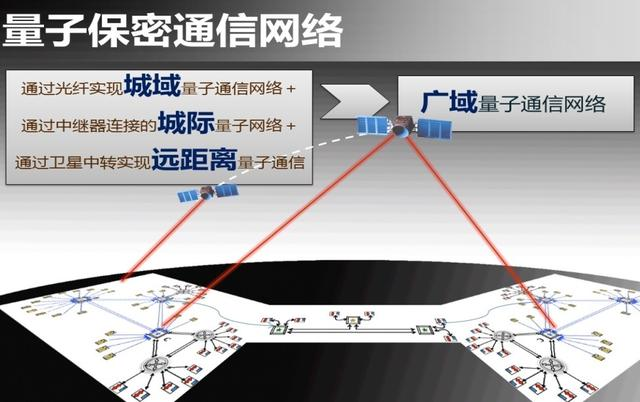
The basis of the security of this process, in addition to the uncertainty principle of quantum mechanics, is to pay attention to the fact that the information is loaded on a single quantum, and the classical information is loaded on the massive quantum (a light pulse usually has 10E8 photons). There are fundamental differences .
In the process of eavesdropping, quantum key distribution loses the same signal as classical communication (I understand that the signal that Mr. Cao refers to is the photon that carries information). However, once quantum key distribution is lost, it is lost and cannot be copied. . It is because of the easy loss of signals in quantum key distribution that the author of BB84 used this process to distribute keys instead of directly transmitting information . Because it is stored as a key and then combined with encrypted communication, it is also possible to try Maintain the continuity and stability of communication. From this point of view, the traditional optical eavesdropping technology does not actually cause the disruption of quantum key distribution. Loss of signals is not a problem for quantum key distribution. Quantum communication is not as fragile as Mr. Cao imagined, nor is it necessary to sacrifice. Stability to achieve confidentiality.
Quantum entangled state
The author finds that Mr. Cao has always used the term "communication" instead of "communicative" now, and does not know whether he wants to distinguish between signal transmission and information transmission. From the author's point of view, this is not necessary, because security is ultimately aimed at information, and the back-end part of quantum key distribution processing is also key information . At the same time, it is also capable of eavesdropping as described above and it is capable of doing damage and information security. It is best not to weaken the signal security.
Regarding the large section of Mr. Cao’s “The large-scale quantum communication network is not feasibleâ€, the author read it very hard, because the logic of the argument has never been found, but the author has read several times out of responsibility for the public readers. . The author still quotes the cryptography application department's opinion on the quantum key distribution technology. Their evaluation is “generate and distributeâ€â€”it used to be generated locally and then distributed to multiple users in various ways. It is more difficult and the process of quantum key distribution completed the generation and distribution of keys at the same time, reduced the links, and greatly improved the security efficiency and security. Mr. Cao's view that "clearly distribution is more difficult to negotiate" doesn't know where to come from. As for Mr. Cao’s use of Bennett and Brassard to criticize their achievements that have been inherited and developed by a large number of scholars, the author personally suggests that Mr. Cao should not do this well. He should insist on respecting the logic and the academic character of the practice test.
Make a simple summary and outlook.
Quantum communication does not currently contribute to improving communication robustness, but it does not hamper its value because it improves the wiretapping ability of the wire, and for the enemies who want to cripple the communication network, quantum communication and classical communication. It is a level. In the long run, quantum communication may develop more subtle communication applications because single-photon-level signals are obviously better able to conceal themselves, and laser transmissions in free space are even more likely to block. Great reduction.

Lei Fengwang Note: In order to facilitate readers' understanding, Lei Fengwang attached the password expert Cao Zhengjun of Shanghai University’s mathematics department to an article published in “Caixin.com†(March 22nd): “Whether Quantum Communication Is Unready,†Cao believes that “quantum communication Not perfect, at least not as good as many people say." The following is the original text:
Is quantum communication upside down?First, what is information?
The commonly referred to information refers to symbols, words, images, speech, and so on. This information is usually expressed as a bit string consisting of 0s and 1s in actual communication. For example: the Chinese character "Han" Unicode code is 0x6C49, using UTF-8 rules into binary is. Zhang Shan in Beijing how to send this bit string to Shanghai's Li Qiang? This requires the use of communication signals.
Second, what is the signal?
Communication signals refer to substances that can be used to transmit information, such as radio waves, electrical signals, magnetic signals, and optical signals. The magnitude of the voltage in the circuit can be used to represent 1, 0. Zhang Shan uses a voltage modulating circuit to modulate into corresponding electrical signals. These electrical signals are then converted into optical signals of different intensities or frequencies by photoelectric converters, and then transmitted using optical fibers. During the transmission process, the optical signal will be degraded. The relay server is required to enhance the signal until it is transmitted to the receiving device of Shanghai Li Qiangduan. The receiving device converts the optical signal into an electrical signal and then converts it into, and then uses the corresponding code. The rules are converted to "Han." For ease of description, encryption, error correction coding and other links are omitted here.
In the history of the development of optical fiber communications, there are two crucial figures. Einstein proposed the light quantum hypothesis in 1905 and successfully explained the phenomenon of photoelectric effects. This is the basis of the photoelectric signal conversion principle. In 1921, he won the Nobel Prize for physics for this doctrine. The Chinese scholar who won the Nobel Prize in physics in 2009 was Takahashi. He achieved a breakthrough in optical physics and discovered how to make light travel in optical fibers for long-distance transmission. This achievement finally led to the advent of optical fiber communication systems. . Without Gao Qi’s persistent research, there will be no Internet age today.
Third, what is information security?
Information security includes a lot of content, the most important being confidentiality and authentication . Confidentiality means that unauthorized users cannot read the information contained in the communication signal. From a formal point of view, an unauthorized user only gets a bit string composed of 0s and 1s. He does not know what kind of transformation rule to use to convert the obtained bit string into original information. Authentication means that the user can confirm the identity of the communication partner or the source of the information.
Because the classical state of the photoelectric signal (light intensity, frequency, voltage, etc.) is very easy to modulate and measure, the adversary can obtain the communication signal through the monitor line. Traditional cryptography always assumes that the adversary has stolen all communication signals. In this case, it studies how to prevent the adversary from reading the information contained in the signal or the adversary's tampering with the signal to deceive the user.
Because the adversary basically does not interfere with the original communication signal during eavesdropping, the target user can correctly recover the signal sent by the sender. The sending parties cannot know whether there is an adversary who is eavesdropping. This means that traditional cryptography cannot detect eavesdropping. In terms of confidentiality, the purpose of traditional cryptography is to prevent the adversary from obtaining the information contained in the signal, which is an intellectual means.
Fourth, what is signal security?
In 1984, Bennett, an IBM researcher, and Brassard, a scholar of the University of Montreal, presented a paper "Quantum cryptography: Public key distribution and coin" at an international conference in India. Tossing). The article claims that quantum cryptography can detect eavesdropping and is absolutely safe. Its theoretical basis is the uncertainty principle of quantum mechanics.
The traditional communication signal behavior refers to the voltage value, the intensity and frequency of light, and the frequency of electromagnetic waves. Unlike these behaviors, the signal behavior used by quantum communication is a quantum state, such as the polarization direction of light and the spin direction of electrons. Because an unknown quantum state cannot be duplicated, once the adversary tries to tap the quantum signal, there will be half the chance to change the quantum state sent by the sender, so the receiver will not be able to properly recover the signal sent by the sender.
The sending parties then make a public comparison through a conventional channel. If both parties find that the measured quantum states are inconsistent when using the same measurement scheme, it can be asserted that there are eavesdroppers on the quantum channel. The purpose of quantum cryptography is to prevent the adversary from obtaining signals, which is a physical means.
V. The relationship between information security and signal security
The opponent cannot obtain the signal and naturally cannot obtain the information contained in the signal. Therefore, a communication system is signal-safe and must be information-safe. This is the origin of absolute security in quantum communications. However, in the situation where an adversary is involved, a communication system cannot necessarily ensure that the target user obtains the correct signal while preventing the adversary from obtaining a signal, that is, the system is unstable.
What is the primary purpose of communication?
The primary purpose of communication is stability , ie the target user can correctly recover the signal sent by the sender. Although information security is important, it is unnecessary for most communications, such as an ordinary email, an ordinary telephone conversation. Eavesdropping is not the purpose of communication.
Usually, it is always assumed that the adversary is present, whether he is eavesdropping on the signal or falsifying the signal.
Seven, signal security and communication stability are incompatible
Cryptography always assumes that the adversary has more physical means than the receiver. Therefore, if a communication system physically deprives the adversary of the ability to steal signals, then it cannot necessarily guarantee that the receiver obtains the correct signal. In other words, the stability of the communication system and the signal security are incompatible.
Once an adversary engages in quantum communications, it will inevitably destroy the quantum signal. Even a destructively small eavesdropping will destroy the quantum signal and prevent the recipient from obtaining the correct signal.
Just to be honest, there are no quantum communications when eavesdropping! Is it safe to have a communication system that is not an easy task with an adversary?
Eight, information security can be compatible with the stability of communications
Although an information security system cannot physically weaken the adversary's ability to intercept signals, it can intellectually ensure that the adversary cannot obtain the information contained in the signal, that is, the stability of the communication system is compatible with the information security.
Nine, large-scale quantum communication network is not feasible
The BB84 protocol proposed by Bennett and Brassard has always been called quantum key distribution (QKD). This name is wrong. The correct name should be quantum key agreement. They did not realize the difference between key distribution and key agreement. Key distribution is the distribution of pre-existing keys. Key agreement is a mutual key agreement between users through information exchange, this key does not exist in advance. Obviously, the former is more difficult than the latter.
Neither Bennett nor Brassard is a professional engaged in cryptographic research. The basic requirements for communications seem to be incomprehensible. They did not realize the difference between signal security and information security, and moved against technological trends. They proposed so-called quantum cryptography based on physical techniques rather than on intelligence. Although their successors published many articles and experiments successfully attracting public attention, they cannot change the fact that large-scale quantum communication networks are not feasible .
Lei Feng Net Note: Reprinted please contact the authorize and retain the source and author, not to delete the content.