The 2016 Artificial Intelligence Hunan Forum and the unveiling ceremony of the Zixing Institute of Artificial Intelligence, many top experts from home and abroad gave us a report at the conference. Institute of Automation, Chinese Academy of Sciences researcher at the National Laboratory of Pattern Recognition, president of Tianjin Institute of Industrial Science and Technology Bureau of Intelligence to identify Sun Zhe, a researcher on South iris recognition this topic a detailed explanation.
This year marks the 60th anniversary of artificial intelligence. Iris, face, and fingerprint recognition are more practical artificial intelligence, and they are also several directions in which development and use have been relatively successful. Today's smart phones are basically unlocked by fingerprint recognition. The new mobile phones recently released by Samsung will be unlocked by the iris. Therefore, many people do not know much about iris recognition. I will give you a popular science.
What is an iris?
The iris is an annular membrane located between the black pupil and the white sclera on the surface of the human eye, and exhibits abundant visual features such as spots, stripes, filaments, coronal cavities, and crypts under infrared light.

Now the identification of people's identity is mainly face recognition and fingerprint recognition. In fact, the iris has a great advantage .
1. Uniqueness: The formation of the iris is mainly determined by the random factors of the embryonic development environment. The random distribution of the details in the iris texture determines the uniqueness of the iris pattern. The iris has a unique texture structure, and the details of the iris feature degrees of freedom It is several hundred orders of magnitude, so it can uniquely identify an individual.
2. Stability: The iris texture is stable after eight months of birth and remains unchanged for life.
3. Non-invasive: Acquisition is non-contact and may be obtained from a distance.
4. Security: relative fingerprints, face features are not easy to steal. Most of the iris needs to be identified in the infrared, because the iris is between the black pupil and the white pupil, and most Chinese iris pigments are below the near infrared to show detailed features and can accurately identify a person's identity.
A brief history of iris recognitionIn 1936, when an ophthalmologist discovered that each individual had different irises, he found that irises could be used for face recognition. In 1985, two other ophthalmologists applied for the first iris recognition patent in the United States. They thought that the irises could pass. Computers to achieve, but they do not know how to achieve, then a researcher at the Harvard University John Daugman invented the first iris recognition algorithm, he is the iris recognition can be expressed in the form of an algorithm, and success The realization of iris recognition.
Then, in the 1990s, some products with iris recognition were developed. Iris recognition was later proved to be a very safe and reliable identification technology. It has been widely used in various fields, including customs, airports, and national IDs. At present, there are three countries as the identity of the identity of the iris, such as India, each person has assigned a number to collect the iris, now has 1 billion collected iris recognition features, applied very successfully in India, Mexico, Indonesia, and now their national identity cards are also With the addition of iris features, the Institute of Automation of the Chinese Academy of Sciences began to study iris products in 1999. Later, we invented the iris application of mobile terminals. The history of the development of the iris is probably.

At present, the application of iris recognition is very extensive. Whether it is the physical space or the cyberspace, as long as personnel identification can be used, including irises that can be used for security clearance, or irises that are used for security against terrorism, some terrorists can Make-up can be easily disguised, or fingerprints can be replaced with scalding, but anti-terrorism requires precise identification. The iris is an important method. At present, our technology is also able to withdraw money from overseas bank self-service cash dispensers using the iris ID card.
In addition, Samsung’s newly released mobile phones use iris recognition, and Alipay also recognizes irises. They also clearly define the direction in which the iris is used in the future. Because fingerprints can be counterfeit, it is possible to steal funds from Alipay through fraudulent fingerprints. Fingerprints including touched tea cups can be stolen because of security attacks. In the administration of public security and judicial prisons, including coal mine workers, attendance is used, and in terms of access control, the iris also has broad application prospects.

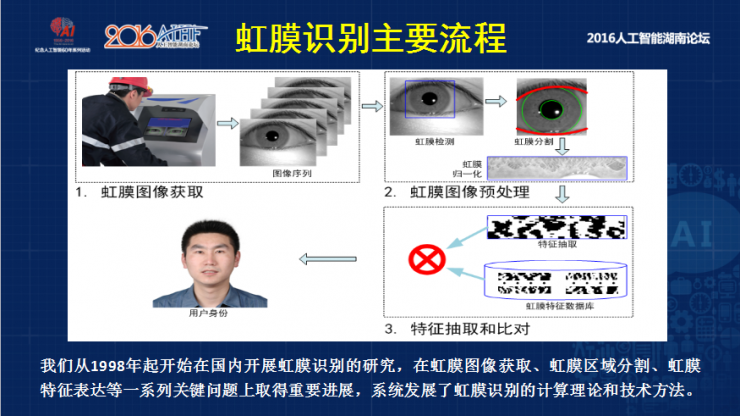
The first step is to obtain the iris image . The iris image acquisition is an ordinary camera can not capture a clear iris texture, because people's iris physical size is relatively small, and the need for some near-infrared light.
The second step is the processing of the iris image . We need to segment it effectively and then normalize it.
The third step is the comparison of iris image features , which is also a key step for the iris. In 1998, we developed the theory and method of iris calculation.
Iris image acquisition :
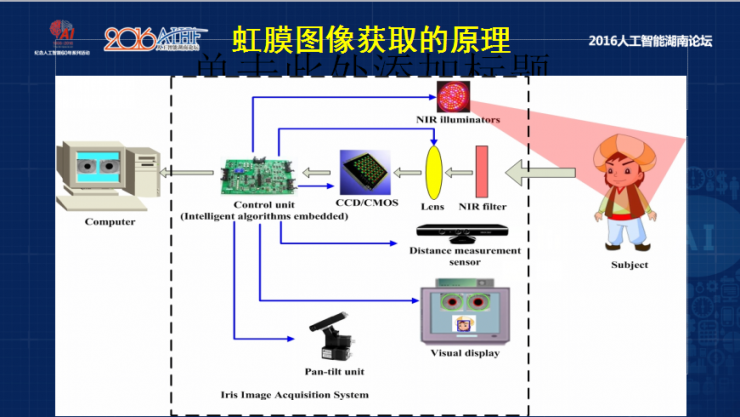
First to introduce the iris image acquisition process, the iris image acquisition is a challenging problem has, first, small physical size, depth of field causing the imaging system is relatively small, then the imaging process the user's eye with a camera on the optical axis, effective Focusing is not very convenient, that is, traditional technologies face great challenges . For example, after wearing the eye, there will be interference of other factors such as reflection, so the iris image acquisition is a bottleneck for iris recognition.

The principle of iris imaging is mainly to adopt a near-infrared filter for imaging after imaging system, including some visual feedback, distance between human and camera . This iris system is a sophisticated automated system, which is an iris image acquired under different conditions. Our Oriental iris texture uses a near-infrared 800-nanometer light source, and the iris image is the clearest.
Currently, the iris recognition system is mainly close-ranged . For example, OKI was the earliest hand-held, iris-used equipment for notebooks, including such portable iris imaging systems, including iris imaging devices. At present, companies also develop long distances. For example, people can collect iris textures between 1 m and 3 m. This is more convenient, and it is also an important trend in security clearance. Major scientific research institutions and scientific research institutions, some companies in the United States, Companies such as Aoptix, Eyelock, and Sarnoff have all developed close-range iris systems.
There are four leaps in the acquisition of iris images . We started from 1998. We achieved it from scratch in 1999. At that time, we bought equipment from the United States. They did not sell us. Later, we passed our independent research. In 2001, we had With great progress, we have achieved monocular-to-eye collection. New equipment was made in both 2006 and 2008. Later, we developed a light-field camera that can take pictures and then focus on them.
Now we develop the iris recognition technology for mobile terminals. This is our latest development of mobile phone iris recognition. This is an iris recognition registration. It is very convenient as long as two or three seconds are available for iris registration. The first iris safety mobile phone was released earlier this year. It is in use in the national security department, including iris equipment with independent intellectual property rights. We have also built our own iris project database. Currently, there are 16,000 research teams applying for it, including With a variety of databases, we have greatly increased the activity of the iris research field through the sharing of iris images.

Iris image processing
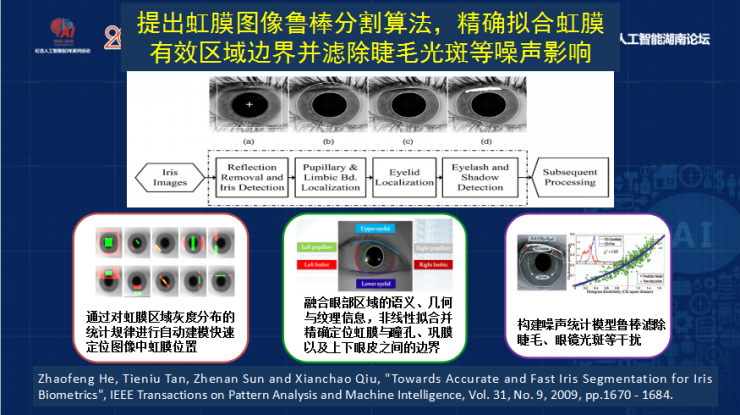
After collecting the iris image, we need to preprocess the iris image by reflecting some of the iris image above, including determining the initial position, which is the iris detection, and then positioning the iris and the inner circle. Sometimes the iris is not completely round. Including the detection of eyelashes and eyes, we also proposed a new method that can automatically model the iris according to the law of distribution, and then combine the texture, the edge of the iris, the boundary of the upper and lower eyelids, and then use some models to filter these eyelashes and spots.
Iris image feature comparison
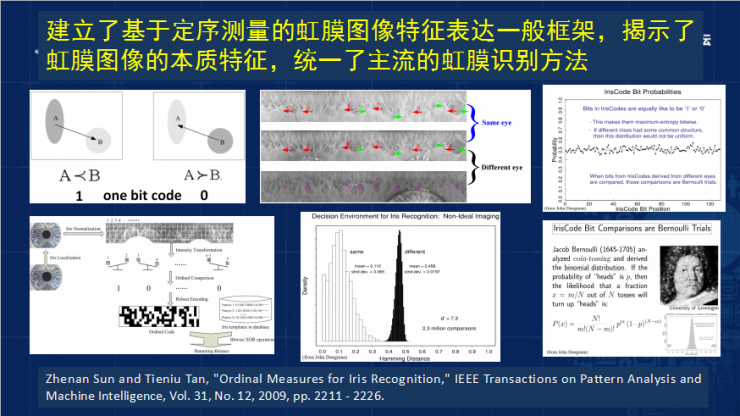
At this time, how to code the iris features, the traditional iris recognition methods are more complex, we propose a relatively new and very simple and practical, the sequencing speed measurement feature is very fast, is to calculate the absolute value between the image region to calculate which Which area is brighter and which area is darker.
These codes are in accordance with the binomial distribution, so that it can be determined that the distribution of matching scores obeys the binomial distribution if the iris is matched by different users. The Hamming distance match score can be very high. Most of the same person, even with some noise, can match the sequencing measurement. This is easy to identify, and the calculation speed is very fast. Later, we proposed the linear programming to solve the problem of the selection of sequence measurement features in the iris and palmprint images, and obtained the best recognition effect in the mainstream iris and palmprint image databases.

After completing the identification of iris technology, we have applied the management of prisoners in prisons, airport security inspections, family planning, anti-terrorism, and foreign cash machines after the transfer of technology transfer. Iris security phones will also be released this year. Although the iris has achieved good recognition results after years of development, it does not necessarily completely solve the problem of iris recognition, because in a complex scene, especially in the case of long-distance, multi-target including communication, how accurate is it? Identifying a person's identity also requires a lot of research.
Including users in different postures and speeds, different lighting environments, and so on, are the future development direction of this system. Especially under the network conditions, there are omnipresent and new opportunities for iris recognition, such as iris collection and recognition beyond 35 meters or even 10 meters, including how the Internet and mobile Internet can challenge mobile phones. We believe there are three challenges: First, how to meet the challenge of convenience. The second is a robust challenge. The third is the challenge of security.
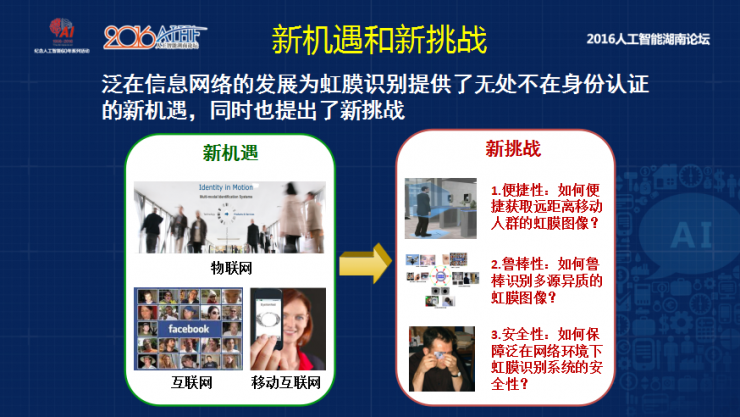
Although the internal security of the iris is much more secure than fingerprinting and human face, it is also possible that others use this kind of iris, art or glass eyeball, or wear contact lenses to enter the iris recognition system. Therefore, the iris needs to be from close to distant, from passive imaging to active imaging, from static imaging to dynamic imaging. In the future, regardless of the circumstances, we can collect multiple people's irises at the same time, from long-distance to close-range, and even humans can present 3D faces, including imaging acquisition and user cooperation. I think that innovations in the biometrics of the irises also require innovation. Because the objects and distances of the irises are ever-changing, it is difficult to ensure that high-quality irises can be acquired each time with a fixed pattern to cope with changing scenes. Imaging.
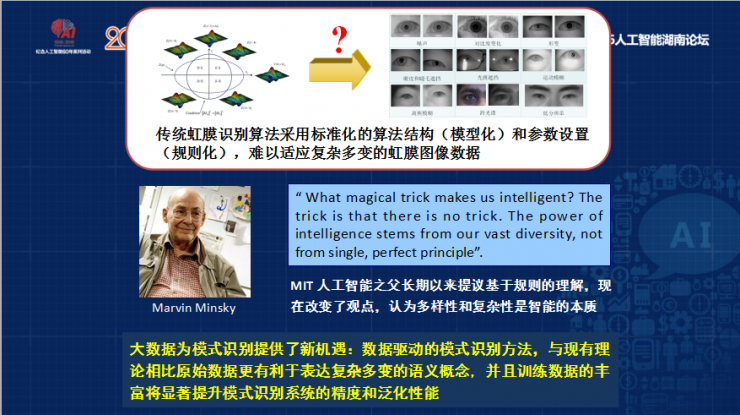
Limitations of Existing Iris Recognition TechnologyTherefore, we believe that all the problems, feelings and knowledge that are now so big are one-way processes . Imaging is done for imaging, and recognition is done for recognition. When the two do not consider, it means that the feelings and knowledge are isolated from each other because we During the imaging process, the sensor frame can be dynamically configured because the imaging devices were always fixed, including the focal length and aperture.

Later we want to make a living, that is, dynamic configuration can be adjusted according to the environment itself, called dynamic configuration of bio-sensing framework . Driven by top-down knowledge, the optimal parameters are selected by the task to capture the best image. During the identification process, it is also bottom-up data driven, and then under the big data drive, a deeper neural network method can be used to get a better recognition model, because the previous recognition model is an artificially adjusted filter parameter and is difficult to deal with. Complex and varied iris imaging, so the recognition algorithm should be adaptive.

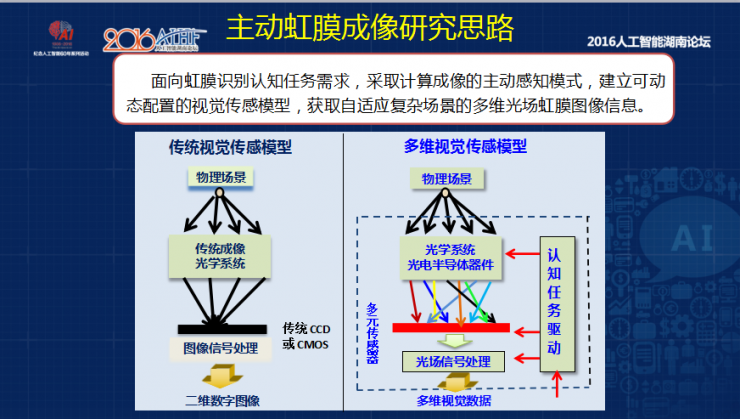
For the needs of iris recognition, we use computational imaging active sensing mode to establish a dynamically configurable visual sensing model and acquire iris imaging information in multidimensional light fields. The imaging process is driven by cognitive tasks and is multidimensional. In the signal processing stage, multidimensional signal processing is performed to calculate. For example, there are calculations in the imaging process, and there are imaging parameters to drive the recognition process. In this case, we introduced the cognitive needs of the identification task during the imaging process to perform targeted iris information detection and establish the identity of the iris texture imaging.

Computational light field imaging
We have researched and developed computational light field imaging. The basic idea of light field imaging is to record the direction of light and the intensity of recording light simultaneously during the imaging process. In this way, three-dimensional perception can be obtained, and the image can be first focused and then focused, and computational imaging can be used. The mode can be used to calculate the refocusing of targets in different positions. In this way, different people's irises can be obtained, so that one image can take multiple human irises.

Light field camera
We have also successfully developed a light field camera and presented the three-dimensional information through a computational model, and can achieve iris imaging of multiple targets at the same time because the original iris imaging uses the first imaging after focusing, and then the iris imaging process can With live test. For example, it is very convenient to use a piece of white paper to automatically recognize the true iris or the fake iris according to the eye area and the focus area.

Data Driven
As the father of artificial intelligence Minsky, he believes that the diversity of data to describe the smart model is more effective, because the nature of the iris is diversity and complexity, so we propose data-driven, that is, using the data neural network model to identify large Data to define such a method. For example, using artificially set rules to perform iris image segmentation, now simply using machines to learn big data models will increase by 19%, so that iris recognition concept elements and data definitions can be achieved, including such noise iris image segmentation. Realized very good results.
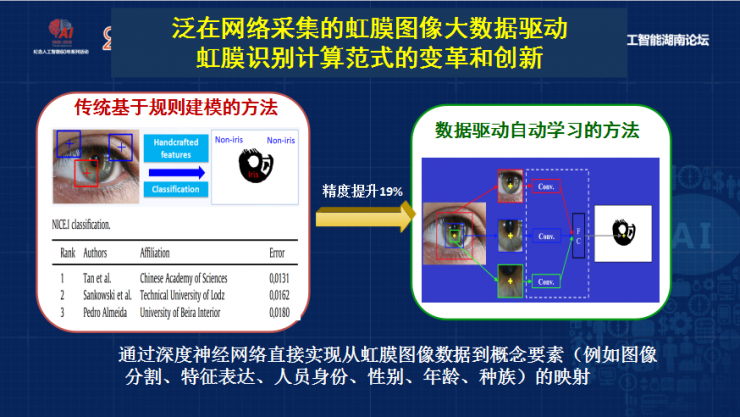
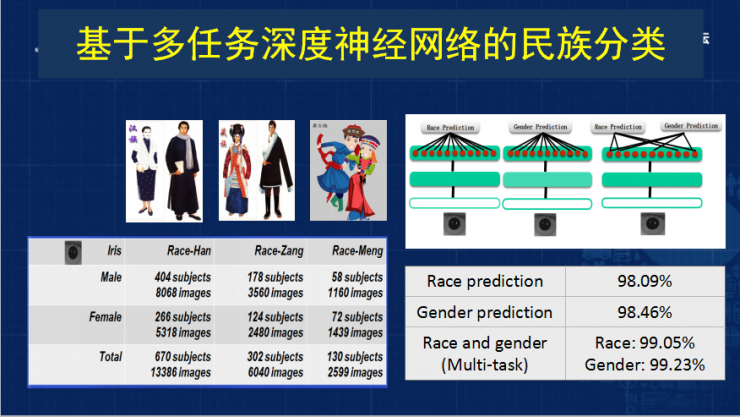
And we use this method to classify this nation at the same time. If it is a single neural network with only 98% accuracy, but the iris network can achieve 99% accuracy, we use the deep neural network to use the iris image because the iris image can From the Internet or mobile phone equipment manufacturers, this imaging has a difference. Overcoming these differences, we have also studied many methods before. We use the common space to express the model. Later we used data-driven, that is to say, depth. Learning to do iris image recognition is also a much higher accuracy than traditional methods.
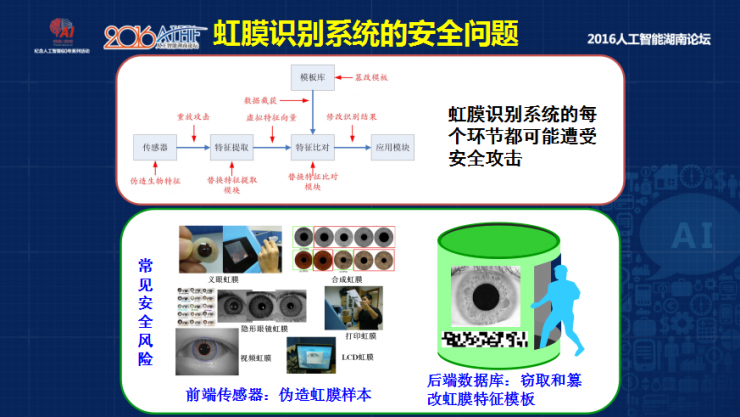
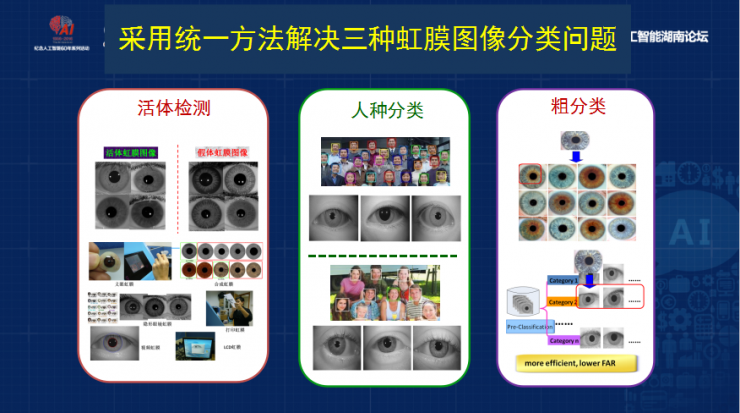
The last question will talk about the iris system will face some security problems in the future, because the iris is an information security system, each link may be subject to security attacks, for example, the sensor can forge data to attack, including feature extraction and sign matching There will be security attacks, with the focus on solving two security analyses . For example, how to identify and recognize the front-end fake iris texture, how to protect the iris signature template at the back end, and protect the user's privacy.
Front-end fake iris texture recognition and judgment method - living body recognition
In order to identify fake iris textures, we used a live detection method. In the live detection method, the main method currently used is the texture classification method. The iris collected by a real user is very natural and round. Then the iris texture of the prosthesis, the imaging will form some rough texture, because we adopt the method of texture classification. To make a difference.
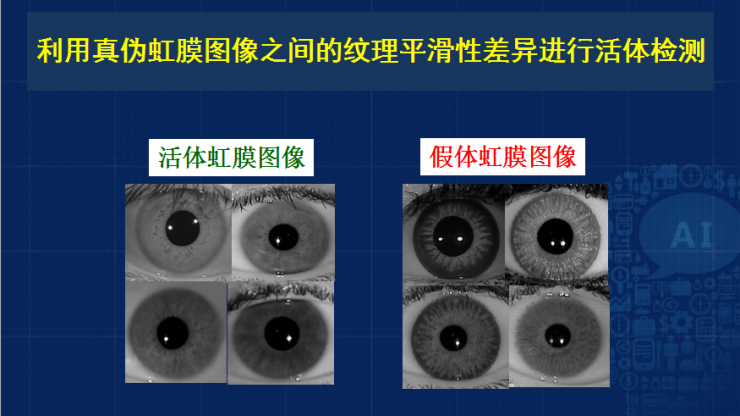
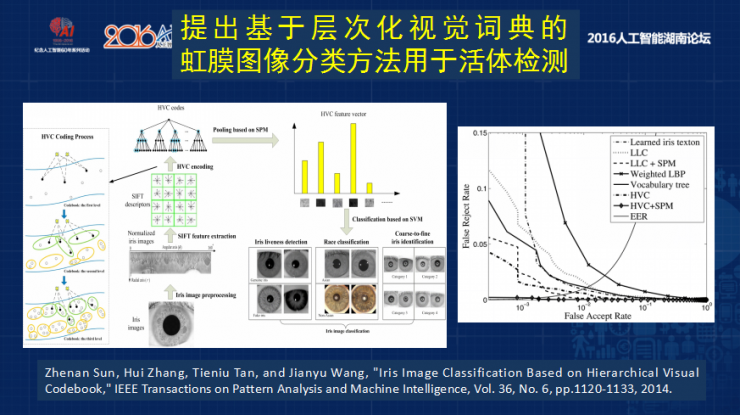
Our live detection methods are also used in human classification and large-scale rough database classification . They have achieved very good results. We use a lot of people's iris big data to automatically implement a hierarchical visual motif dictionary , and then on this projection. To classify, current foreign banks have such needs, because more than 99% of live detections can detect fake pupil iris images, and can automatically judge or automatically alarm for contact lenses, and the same model can not only solve the problem of iris live detection but also Realize the classification of race.
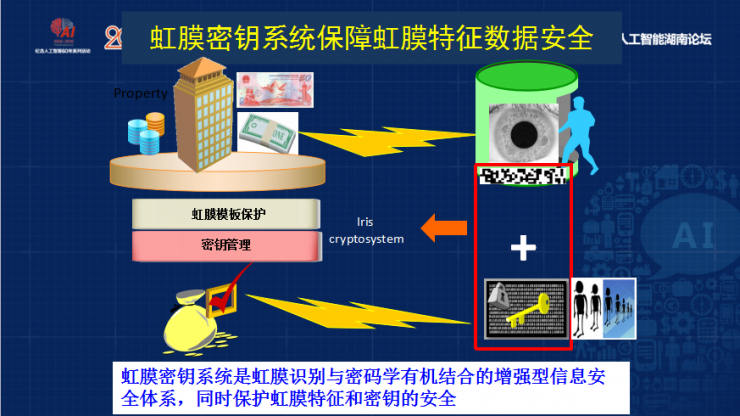
Back End Iris Feature Protection - Iris Key System
For example, in the traditional iris recognition, the iris is not related to genes. Later, our study of irises is related to genes. Asians are very different from the irises of Europeans. We can use automated classification methods to reach 99. % of the accuracy, you give me an iris image I know whether it is Asian or European, we also put forward the system of iris key, we combine it with information security, we propose the method of iris key, at the same time Protecting the iris template can also protect the key. The iris key is a security system that combines the recognition of iris and cryptography. It can not only ensure the security of the iris feature and key, but also adopt the method of fuzzy promise.

The basic principle is that the 512-byte iris feature encoding can be computed with the key's error correction code generation key code, and the result of the operation is a safe result, and this result is difficult to attack unless you know my key. However, as long as it is the result of the iris comparison, even if it cannot be 100% compared, if the error error is within a certain range, the key can be solved using this error correction code, and this can be achieved. The iris feature is revocable.
For example, the iris template can take a new template to protect the encryption. In this way, the iris template can be protected. In the actual process, different images collected at different iris times cannot be matched on one hundred percent, and some errors may occur. Error correction coding to overcome, in addition to enhance the degree of invasive keys, we passed the imaging features and extraction module, take several kinds of error correction coding, can improve security, this iris key system can achieve 800 The key system is embedded, and the accuracy is very high.
Our team is systematically innovating from the source of iris information acquisition, opening a complete chain of iris recognition from scientific research to industrialization, practicing acquisition devices, data resources, recognition algorithms, integrated systems, and applying a technical route, although we have achieved Some progress, but iris recognition We think that from the controlled scene to the complex scene, there are still many problems that need to be solved. We need to solve the problems of convenience, robustness, and security. We will also make further efforts to improve Nice iris system.
Q & A sessionQuestion: In the process that you just mentioned mentioned the problem of recognition accuracy, I asked the accuracy is the results obtained in the database?
Sun Zhenan: The result of the experiment was in hundreds of individuals, including Han, Mongolian, and Tibetan. This database has a description. There are more than 400 Han people, more than 400 men, more than 200 women, and 178 Tibetans. Men, 124 women, Mongolian people are relatively few, there are 58 men and 72 women, and the amount of data has more than 20,000 pictures.
Question: In addition to these tests, what is the maximum amount of tolerance in other databases? It is to maintain 90% accuracy.
Sun Zhenan: We have also measured that we have measured over a thousand people can basically reach more than 99%, for example, simply define two categories, such as the accuracy of the Orientals and Westerners is also very high, because the Oriental and Western people texture Distribution and characteristics are still different.
Question: Did you just talk about the iris recognition team's achievements in the future? In addition to the several iris-recognized phones just mentioned.
Sun Zhenan: We recently applied for a national key R&D program. There is a project in the cloud computing and big data special project. We will achieve tens of centimeters of multi-modal iris face gait image recognition in the future, that is, there is an urgent need for them to maintain stability in anti-terrorism. Demand, because there are many extremists, his face is cosmetic, the name is changed, the fingerprints are erased completely, and the identity of these people cannot be confirmed. The next person we will be in the public safety field to do this system, basically giving The key personnel are collecting irises. After going abroad, they basically cannot change the iris. Unless they blind their eyes, China’s anti-terrorism still has how to identify the person’s identity from a remote location in the surveillance environment. There are still many iris systems. Field to study.
Question: I would like to ask, Cai Lan and contact lenses have an impact on the iris recognition system?
Sun Zhenan: If you wear a color box or a beautiful pupil, it will have an influence. This texture is not the texture of this person. It is the texture that is superimposed on it. We must accurately judge it. For example, our system can automatically identify the foreign bank and your imaging at that time. Is wearing a color pupil or a beautiful pupil, our system can automatically identify, must ask this person to take off the color pupil or a beautiful pupil.
carbide Twist drill are the most common type of drill bit and are used for everyday drilling in all types of material. They are also the most confusing due to the sheer number of size, tip, and material specifications.
hese are the most common twist drills and are a good compromise between length and strength
The range of high-precision solid Carbide Drills makes OPT one of the world's leading tool manufacturers. OPT high performance drills are available with or without internal cooling. They are delivered with modern
coatings (including diamond coatings) which are adjusted to each material, which results in vast tool lives. By means of their optimization for various purposes, the drills build a product range which enables economic drilling for a broad spectrum of applications.
Solid carbide drills by OPT are designed especially for metalworking of steel, stainless steel, hardened steel < 70 HRC, titanium, inconel, aluminum and GRP/CRP. All solid carbide drills with diameters up to 3 mm and drill depths from 8 x D are provided with a polished flute as well.
Flexible in order quantity:
Samples can be provided before mass production, and MOQ can be discussed accordingly.
PRODUCT DETAIL:




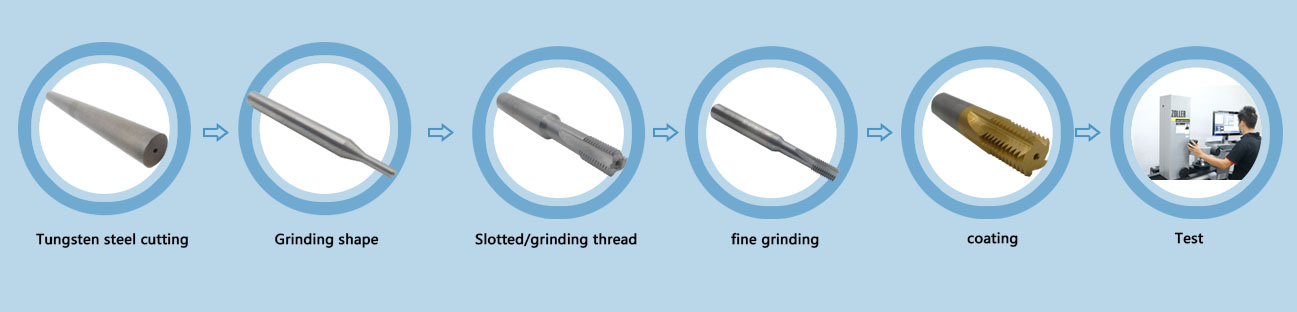
PRODUCTING PROGRESS:
PAYMENT AND DELIVERY:

PRODUCT EQUIPMENT :

ABOUT US :
We are specialize in manufacturing PCD diamond tools and Carbide tools. Our major product inclulde PCD Inserts , PCD Reamers , PCD End Mills, PCD Taps, Cabide Inserts,Carbide Drills, Carbide Reams, Taps etc.,
We also offered customized cutting tools per drawings, and provide package according to customer requirements. We manufacture a series range of cutting tools for machining of Cast iron, Aluminium alloy and Non-Ferros metal, it is widely used in all major sectors like Automobiles, Engineering, Aerospace, Aviation and 3C industry. Premium quality of raw material is used in the production and strict examination during processing with advanced equipment, so our client are satisfied with our reliable quality and on-time delivery.
Our best selling of cutting tools include PCD Inserts, PCD End Mill, PCD Ball Nose Mill, PCD Reamer, Carbide Taps, Carbide End Mill, Special Form Cutter and many more. For these years we have been made a large forward in the technologies of manufacturing cutting tools. With high quality on performance and price, our product sells well both on domestic and overseas market. And we will always focus on the quality and best service, to make long business relationship.

quanlity control:
We have dedicated team of quality control and precise equipment to keep good and stable performance for our products and processing services.

Carbide G Drill, Twist Drills,Carbide Twist Drills,Carbide Tipped Drill Bits,Carbide Twist Drill Bits
OPT Cutting Tools Co., Ltd. , https://www.optdiamondtoolss.com